Homework 4 - Network Layer
Submission information: This homework assignment is due at the start of class on the due date. You must turn it in electronically via the companion Sakai website. Simply upload a document in PDF format, or type your solution directly into the Assignment submission box.
Problem 1 - Gateways (Routers)
- When you configure a default gateway in your desktop PC, what is it used for?
- What is the role of gateways in the larger public Internet?
Problem 2 - Think Like a Computer: Address and Netmask Bits
Given the IP address 93.32.213.53 and a netmask 255.255.255.128, specify
- The length of the subnet or network address in bits
- The subnet address
- The broadcast address in the subnet
- The lower and upper bounds of valid IP addresses in the subnet
(hint: can the subnet address and broadcast address also be used to represent computers in the subnet?)
Problem 3 - Think Like a Computer: Subnets
Assume a host using IP is connected to an Ethernet local area network.
- Short answer: How does the host distinguish between hosts on its local subnet, and hosts not on its local subnet?
- Imagine three different scenarios. In each scenario, a host computer sends out 1 packet to a particular destination IP address. In each scenario, the host's own IP address and netmask are different, along with the destination IP address being targeted. For each scenario listed in the table below, state if the destination is on the local subnet, or not.
| Scenario | Host IP Address | Host Subnet Mask | Destination IP Address | Destination in Same Subnet? |
|---|---|---|---|---|
| 1 | 192.168.1.15 | 255.255.255.0 | 192.168.1.218 | Yes or No? |
| 2 | 147.18.219.61 | 255.255.255.192 | 147.18.219.64 | Yes or No? |
| 3 | 147.18.219.61 | 255.255.255.192 | 147.18.219.59 | Yes or No? |
Problem 4 - Address Resolution Protocol (ARP)
- In an IP network, why is an ARP query sent within a broadcast Ethernet frame?
- In an IP network, why is the ARP response sent within an Ethernet frame with a specific destination MAC address?
- Describe one example of a security problem affecting the ARP protocol. Your answer must explain in detail why the protocol is vulnerable.
Problem 5 - Interaction of IP, Ethernet, and ARP
Consider three LANs interconnected by two routers:
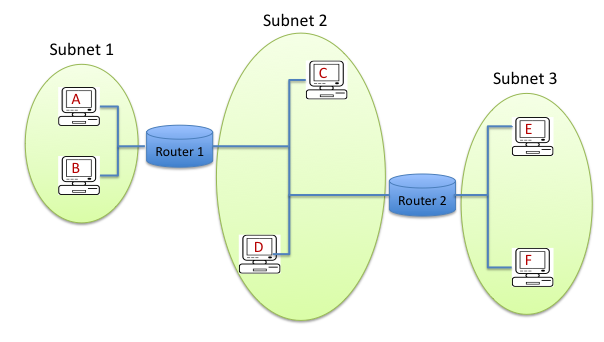
- Create a table summarizing information for every network adapter on the network. (Hosts A-F each have one network adapter, and every router has multiple network adapters, one per subnet). The table should contain columns for the host/router name (shown in the figure) plus "realistic-looking" IP and MAC addresses that you generate. The addresses should follow these rules:
- For subnet 1, use IP addresses of the form 192.168.1.xxx.
- For subnet 2, use IP addresses of the form 192.168.2.xxx.
- For subnet 3, use IP addresses of the form 192.168.3.xxx.
- MAC addresses can follow any format you see fit.
- Consider sending an IP datagram from host E to host B. Assume all the ARP tables are up-to-date. Enumerate all of the packets that are necessary in the order that they are sent. Include details such as source and destination IP and MAC addresses. Use the table format shown below.
- Repeat step (2), with the new assumption that the ARP table in host E (the sending host) is empty, and all other ARP tables are up-to-date. Enumerate all of the packets that are necessary in the order that they are sent. Include details such as source and destination IP and MAC addresses. Use the table format shown below.
Table format to use for parts 2 and 3:
| Packet Number | Dest. MAC Addr | Source MAC Addr | Dest. IP Addr | Source IP Addr | Description of packet |
|---|---|---|---|---|---|
| 1 | Use addresses consistent with your earlier answer |
What is this packet? Why is it sent? |
|||
| 2 | |||||
| 3 | |||||
| 4 | |||||
| ... |